Modern SaaS stacks rely on dozens of tools, each with distinct access requirements. For IT and security teams, identity becomes the connective tissue that either holds everything together or quietly introduces risk. That’s where questions around SCIM vs SAML tend to surface.
Both protocols are widely used, often mentioned together, and frequently misunderstood. One governs how users log in. The other governs whether user identities should exist in a system at all. Understanding the difference is essential if you manage identity through Okta, Azure AD, Google Workspace, or Slack-based environments.
This article breaks down SCIM and SAML in plain terms, explains how they differ, and clarifies why most modern SaaS environments end up needing both.
TL;DR
SCIM manages who gets access and keeps users and groups in sync.
SAML handles how users authenticate via single sign-on.
SCIM acts during lifecycle changes; SAML acts at login.
Most secure SaaS environments use SCIM and SAML together, not one or the other.
What Is SAML?
Security Assertion Markup Language (SAML) is an authentication protocol. Its primary role is to allow users to log in to one application using credentials verified by another trusted system. In practice, this enables single sign-on across SaaS tools.
SAML works through a trust relationship between an identity provider (IdP) and a Service Provider (SP). When a user attempts to access an application, the app redirects them to the IdP. After authentication, the IdP sends a signed assertion confirming the user’s identity. The application trusts that assertion and grants access.
Centralized authentication significantly reduces password sprawl. Over 80% of breaches still involve stolen or compromised credentials, highlighting why federated authentication remains critical to enterprise security posture.
SAML is therefore excellent at answering one question: Is this user who they claim to be right now? What it does not answer is whether that user should exist in the system in the first place, which is where SCIM enters the picture.
What Is SCIM?
System for Cross-domain Identity Management (SCIM) is an open standard provisioning protocol. Instead of focusing on login, SCIM focuses on identity lifecycle management: creating, updating, and removing user accounts across systems automatically.
SCIM is typically driven by an IdP or HR system. When an employee joins, changes roles, or leaves the company, SCIM ensures those updates propagate to connected SaaS tools. User accounts are created, group memberships adjusted, and access removed without manual intervention.
From a security and cybersecurity standpoint, this automation is critical, particularly for timely deprovisioning. Gartner estimates that manual identity processes account for a significant share of delayed deprovisioning, a key contributor to insider and post-employment access risk. SCIM directly addresses this gap by enforcing joiner–mover–leaver workflows consistently.
In short, SCIM answers a different question than SAML: Should this user exist here, and what should they have access to?
SCIM vs SAML: What Each Protocol Actually Does
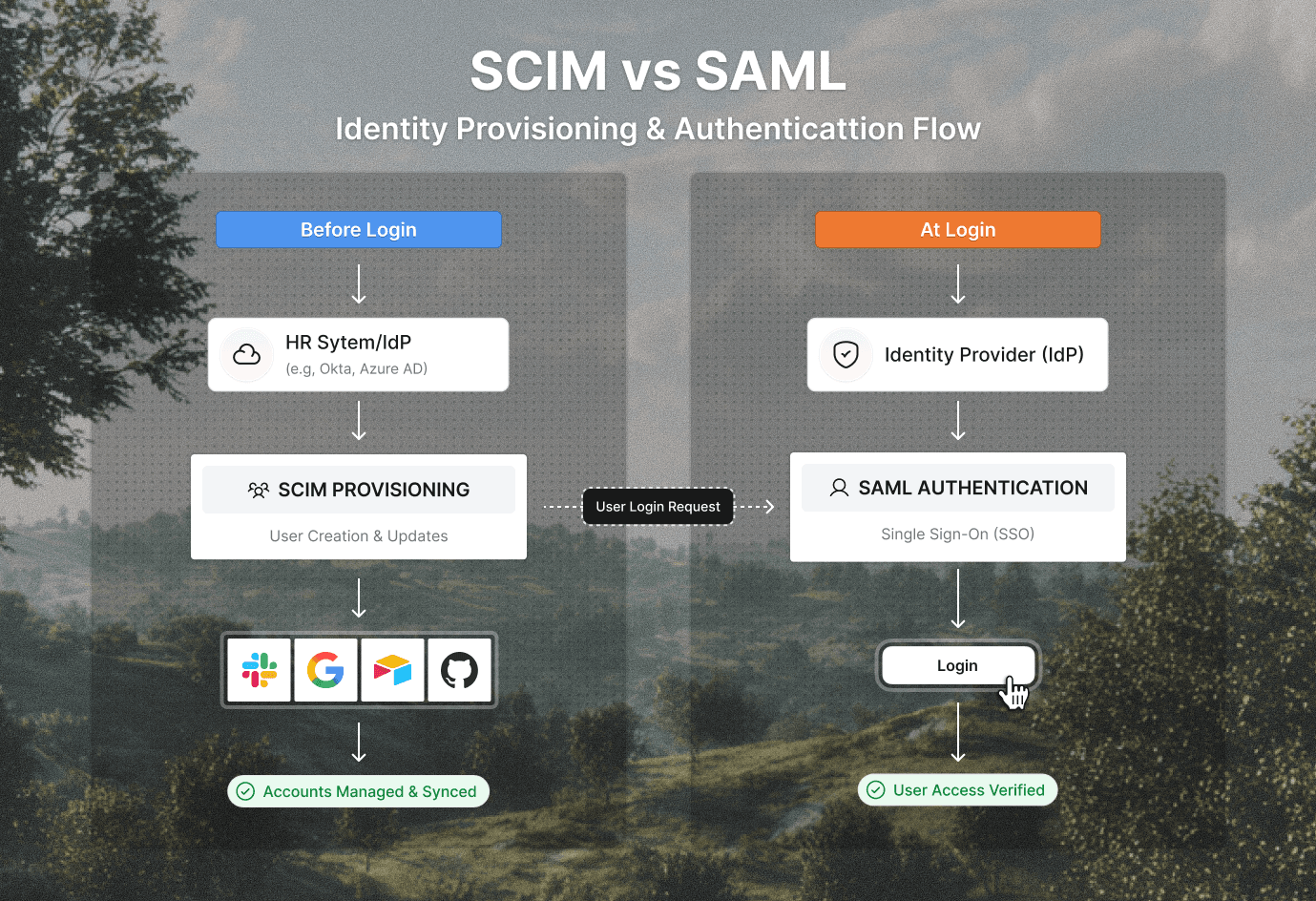
The most effective way to understand SCIM vs SAML is to look at timing and responsibility within identity and access management. Although they often coexist, they operate at different moments in the identity lifecycle.
SAML activates when a user attempts to log in. It validates identity in real time using authentication assertions, typically formatted in XML. Its scope is narrow but critical: authentication and single sign-on.
SCIM operates before login ever happens. It manages accounts and entitlements using REST APIs and JSON through a standardized API model. Its role is broader and continuous, ensuring systems reflect organizational reality as it changes.
Put simply, SAML controls access at the door. SCIM controls who gets a key and whether it should be taken away. Confusing the two creates gaps that neither protocol can address alone.
Why SCIM and SAML Are Complementary
It’s tempting to ask whether SCIM replaces SAML or vice versa. In practice, that framing causes more confusion than clarity. These protocols solve different problems and are designed to work together.
SAML without SCIM means users can authenticate successfully, even if they should no longer have access. Former employees may still exist in applications, relying solely on login controls for protection. SCIM without SAML, meanwhile, leaves authentication fragmented and password-heavy.
This distinction is especially important in discussions around SCIM vs SSO. Single sign-on is an experience enabled by protocols like SAML or OIDC. SCIM does not provide SSO. It ensures that SSO applies only to the right users, in the right groups, at the right time.
When combined, SCIM and SAML create a layered identity model: lifecycle governance paired with secure authentication.
When You Need Both in Modern SaaS Environments
Most organizations reach the point where both protocols become necessary as soon as SaaS adoption scales. A typical modern identity flow looks like this:
An employee is hired during onboarding and entered into an HR system. That data feeds an IdP such as Okta or Azure AD. SCIM then provisions the user into tools like Slack, Jira, or Google Workspace with appropriate group memberships. When the user signs in, SAML handles authentication through the IdP, while offboarding later triggers automated access removal.
This pattern directly addresses common confusions such as SCIM user provisioning vs SAML login or when to use SCIM and SAML together. In nearly all mature SaaS environments, the answer is the same: you use both.
Industry adoption reflects this reality. An average company manages many SaaS applications, making automated provisioning and centralized authentication operational necessities rather than nice-to-haves.
How Ravenna Works With Your Existing SCIM and SAML Setup
Ravenna is designed to fit into this established identity ecosystem rather than replace it. It assumes your IdP already handles authentication through SAML or OIDC, and that SCIM governs user provisioning where supported.
In Slack-first environments, Ravenna respects these boundaries. Access decisions reflect existing identity, permissions, and group structures, while workflows operate within the permissions users already have. There is no parallel identity layer to manage and no duplication of provisioning logic.
This approach allows teams to extend service management and automation capabilities without weakening identity controls. Your SCIM and SAML setup remains the source of truth; Ravenna simply builds on top of it.
Read more on how an AI helpdesk works.
Final Thoughts on SCIM vs SAML
Understanding SCIM vs SAML comes down to recognizing that identity is both a lifecycle and a moment-in-time event. SCIM governs the lifecycle — who exists, what they can access, and when that access should change. SAML governs the moment — verifying identity at login.
In modern SaaS environments, these functions are inseparable. Teams that rely on one without the other often discover gaps in security, automation, or operational clarity. Using both creates a cleaner, safer, and more scalable IAM foundation with stronger access control.
FAQs
What is the difference between SCIM and SAML?
The difference between SCIM vs SAML lies in what part of identity and access management they control. SCIM (System for Cross-domain Identity Management) is a provisioning protocol that automates user lifecycle management, including creating, updating, and deprovisioning user accounts across SaaS applications. SAML (Security Assertion Markup Language) is an authentication protocol used for single sign-on (SSO), allowing users to authenticate through a trusted identity provider (IdP). SCIM governs who should have access, while SAML governs how users authenticate.
Do I need SCIM if I already use SAML?
Yes. Even if you already use SAML for authentication and single sign-on, you still need SCIM for automated user provisioning and deprovisioning. SAML only verifies user identity at login and does not manage user accounts or access rights. SCIM ensures that user identities, group memberships, and permissions stay in sync across systems during onboarding, role changes, and offboarding, reducing security risks from orphaned accounts.
Is SCIM the same as SSO?
No. SCIM is not the same as SSO. Single sign-on is enabled by authentication protocols such as SAML or OIDC, which allow users to log in once and access multiple applications securely. SCIM, on the other hand, is a provisioning standard that manages user accounts, identity data, and access lifecycle events behind the scenes. SCIM supports SSO by ensuring only the right users exist in applications, but it does not handle authentication itself.
How do SCIM and SAML work together?
SCIM and SAML work together to provide a complete identity and access management workflow. SCIM provisions users, assigns group memberships, and automates access changes across SaaS tools before login occurs. When users attempt to access an application, SAML authenticates them through the identity provider using secure assertions. Together, they combine lifecycle automation with secure authentication, reducing unauthorized access and improving SaaS security at scale.
Can SCIM replace SAML?
No. SCIM cannot replace SAML because it does not perform user authentication. SCIM manages identity lifecycle events such as onboarding, role changes, and offboarding using APIs and automated workflows. SAML is required to authenticate users and enable single sign-on across web applications. Most modern SaaS environments use both SCIM and SAML together to maintain strong access control, secure authentication, and consistent identity management.




